As mentioned before, DLL files are related to programs. If error pops up when you open certain program, such as Internet Explorer or third party application, update the program or reinstall it. The update and installation may contain the missing DLL file. Just search for your DLL file and download it from our website for free.
Such abrupt system shutdown can be detrimental to data integrity or file you’re working on. It can be an important assignment or project in Microsoft Word, Photoshop, Excel or any other program. Here, we discuss some essential steps for server hardening that resolve more or less all issues encountered with server msvcp140.dll error management. This will safeguard a server against the vast majority of threats that are presented over the internet.
Major Details Of Dll Clarified
More importantly senior management cannot say this to the press, to a regulator, to a court. Same reason for having state-full inspection firewalls, anti-virus, IDS even though they are less effective now than 10 years ago. We know that the attacker might have a hash of your password –which essentially gives him your password given enough time, regardless of the method he uses to crack it with. Replacing your password will thus invalidate the information the attacker has.
There are more than 200 CMD commands available with Windows. The command prompt can be used to control large parts of the operating system, computer, or drives.
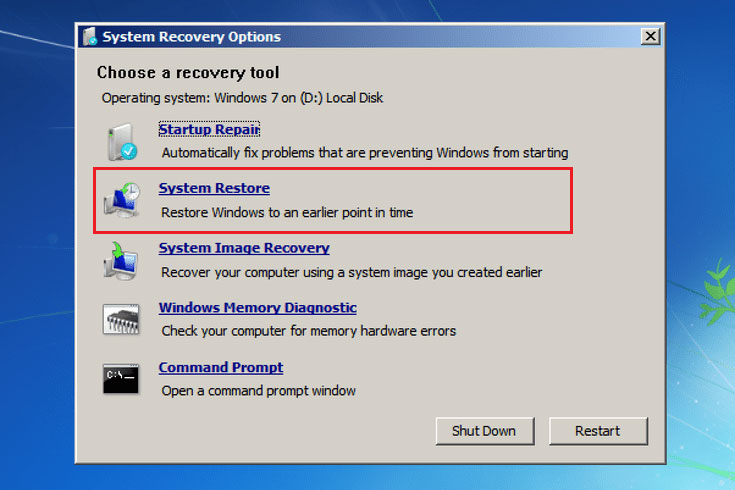
- You must be signed in as an administrator to be able to do the steps below to take ownership of an item.
- In a world where time is money, every agency needs to get the most possible out of its machines.
- Here are the suggestions our Support Engineers provide to our customers to resolve this DLL file error.
In particular, malware is regularly designed to change the values of startup keys so it will be activated each time you restart the PC. Changes to the registry by malware require immediate attention. Microsoft’s Windows is one of the most used operating systems and it has many features that most certainly assert its dominance over the competition. Everything that is done on the computer, be that installing an application, visiting a webpage, etc. is stored in the registry. The Registry is the digital footprint of the user on Windows. It also contains numerous entries that are vital for Windows and shape the way it runs on a daily basis. All the databases are stored in the registry, and hence proper usage of the registry should be ensured.
Deciding Upon Uncomplicated Advice For Dll Files
S0082 Emissary Variants of Emissary have added Run Registry keys to establish persistence. S0115 Crimson Crimson can add Registry run keys for persistence.
This brings up the familiar old Custom sizing options dialog. From there, you can select the scaling percentage you want from the drop-down menu, or drag the ruler left or right to the scaling percentage that suits your monitor. In the right pane, click on the drop-down menu to “Change the size of text, apps, and other items” and select the DPI percentage you want to set for your display. Check the timestamps, you’ll see the modified time has changed as you would expect but still no change to the accessed time. The Appraiser_TelemetryRunList.xml file tells the appraiser which actions to perform.
